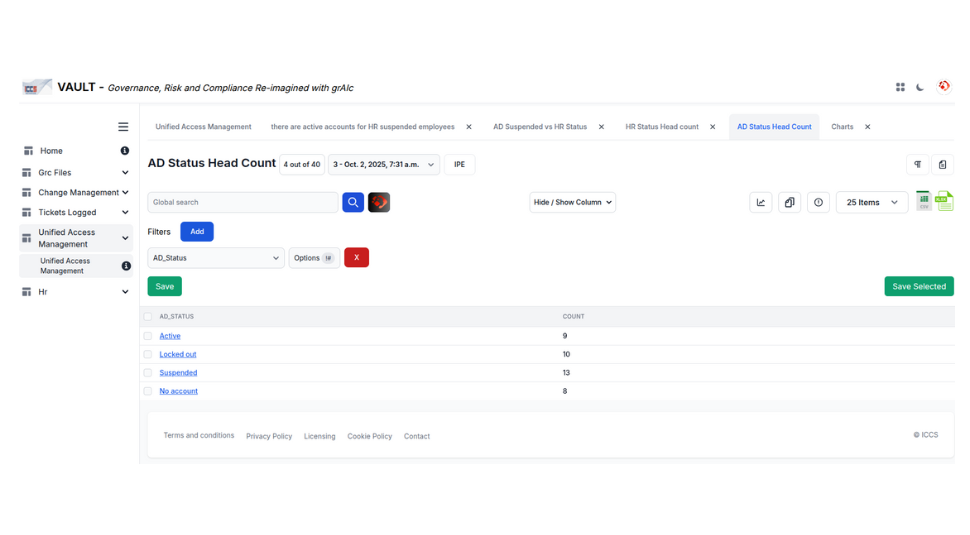
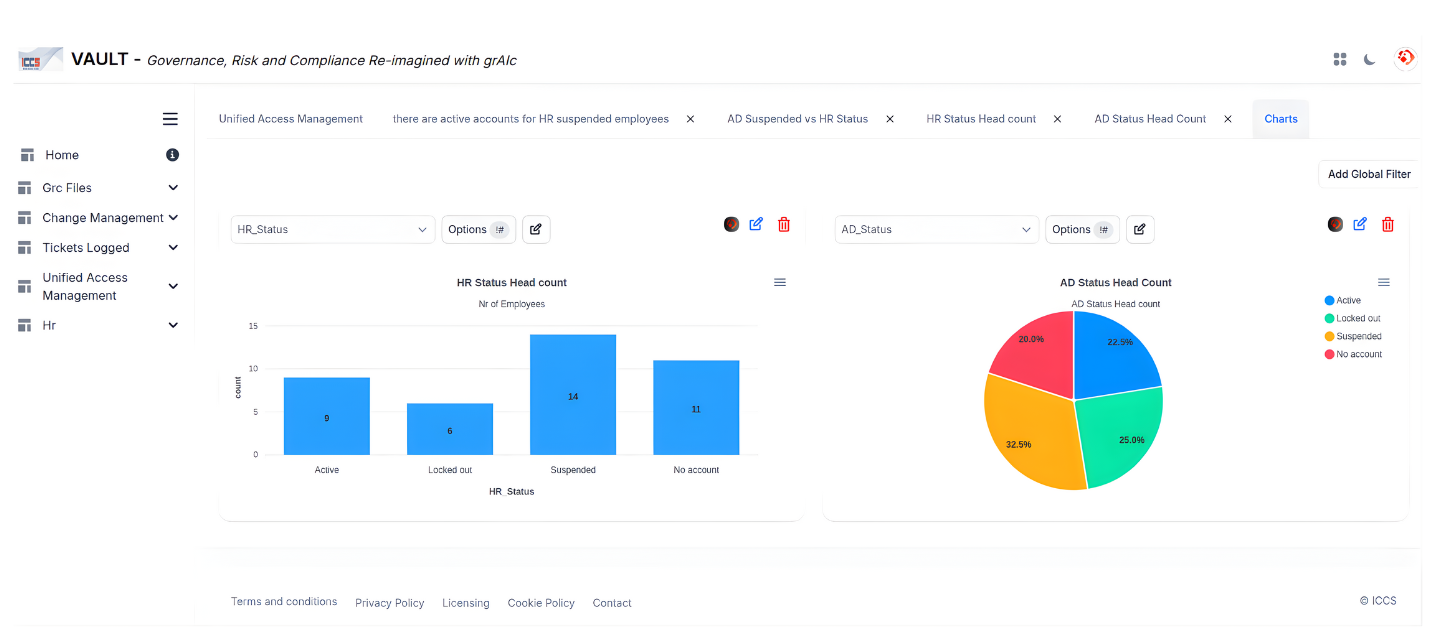
Data Foundation & Pipeline Architecture
Establish a unified data ingestion and processing layer that captures, normalizes, and routes observability data across your entire technology stack.
Details & checklist
Multi-Source Data Ingestion
- Deploy collectors across infrastructure (servers, containers, serverless)
- Instrument applications with telemetry SDKs (OpenTelemetry)
- Integrate network flows, security events & cloud-native monitoring
- Capture business metrics and UX data
Data Pipeline Architecture
- Streaming pipelines (Kafka, Kinesis), transformation, validation and intelligent routing
- Correlation engines to link traces, logs, and metrics
Storage Strategy
- Hot (real-time), Warm (recent), Cold (long-term) storage tiers with retention policies
Data Taxonomy & Standards
- Unified schema, naming, tagging, metadata and SLAs
We Deliver: Operational pipelines, centralized observability lake, documentation of flows/schemas, ingestion & query performance benchmarks.